When it comes to online security terminologies, many people seem not to care. However, considering the risks out there, it is important to be able to identify these threats. Once you know what malware entity you are dealing with, you can easily contain and get rid of it.
In this article, we will discuss everything you should know about one particular threat: the Great Suspender Malware. But before we proceed with the in-depth discussion, let’s first tackle the basics. What is malware and how do you know if you have been infected by it?
What Is Malware?
 You’ve probably heard of this term a hundred times before. But what does it really mean?
You’ve probably heard of this term a hundred times before. But what does it really mean?
Malware is simply a term for any type of malicious software that is designed to bring harm or exploit any network, device, or service. Cybercriminals use this entity to steal data from a potential victim for personal gain. When we say data, this could include personal information, healthcare records, credit card details, emails and passwords.
So, how does malware spread? There are many ways that it could be spread. Among the most popular methods include malicious advertisements, email attachments, fake software downloads, phishing, and infected devices.
Sad to say, there are already thousands of malware entities out there that listing all of them in this article would take days to complete. But the good news is that understanding the common types of malware entities can go a long way in protecting sensitive information and your device.
Below are some of the most common types of malware entities:
- Viruses – They are usually spread via email attachments. Once a victim clicks on the attachment, the device is automatically infected. One of the most popular viruses today is the Soap2day virus.
- Ransomware – This malware type is the most profitable. It’s not surprising why cybercriminals love to use them. It works by installing itself onto the victim’s machine. And then, it encrypts the files and demands a ransom to return the file or data to the user.
- Worms – Worms are notorious for their ability to duplicate themselves and multiply from one machine to another. They generally exploit a device’s security weakness.
- Trojans – These malware entities disguise as harmless applications, luring unsuspecting victims into downloading and using them. Once used, Trojans steal personal information and spy on a user’s activities.
- Spyware – We also have the spyware entity. It is a program installed on a device without the victim’s knowledge. It works by stealing personal information and browsing activities and then sends the information to its developers.
- Adware – Among all the types of malware programs, this one is the lesser invasive. It only attempts to expose unsuspecting users to potentially malicious advertising. Generally, an adware program will redirect a user’s search activities to a website that contains various product promotions.
- Other Exotic Forms – These are notorious entities that are a combination of traditional malicious entities like worms and Trojans. Usually, it appears like a Trojan. But once executed, it attacks like a worm.
The Great Suspender Malware: What You Should Know
Recently, there were reports of a Google Chrome extension that was forcibly uninstalled by the search giant as it was classified as a malware entity. It’s called The Great Suspender.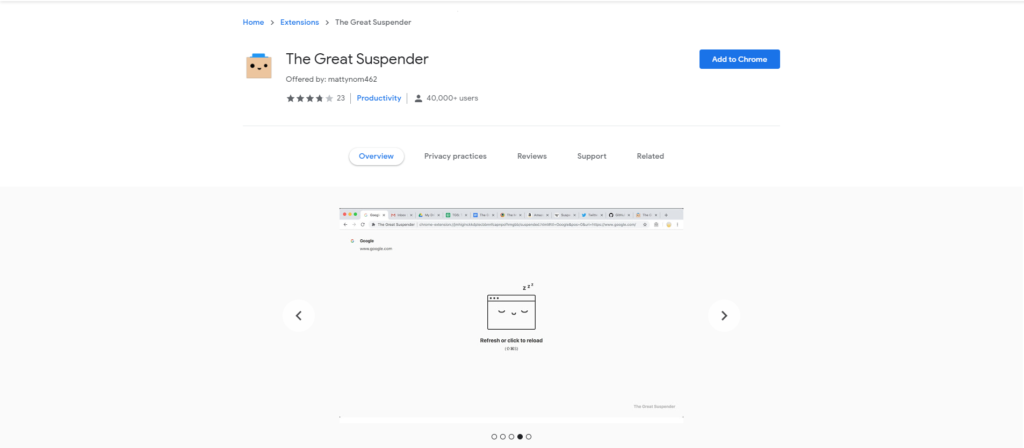
The Great Suspender is an extension that suspends any unused tabs and unloads its resources to reduce Chrome’s memory usage. Once the user accesses the tab again, he/she simply needs to click on it. That way, the tab will be visible once again.
With more than 2,000,000 users, it was obvious that the extension was indeed popular. It has been a highly recommended extension as it helps reduce Chrome’s resource usage.
Unfortunately, there came a point in time when Google had to remove it. Surprised users of the extension were only left with the message “This extension contains malware.” They did not have enough information about what happened or how to recover their suspended tabs.
Well, it is still possible for users to see their suspended tabs. Chrome still has its built-in History feature. However, it’s just sad to see such a useful extension getting removed by Google. Not only did it keep the browser running efficiently and smoothly, but it also automatically closed tabs that were not used for quite some time.
Now, you may ask, what does the Great Suspender Malware do? As of this writing, Google still hasn’t mentioned anything about what the malware does. But even before it was disabled by Google, some users have already raised safety concerns. According to them:
- The developer of the extension injected malicious codes into it.
- There were changes that have been applied to the extension, which were not disclosed. However, some users suspect that the extension was connecting to several third-party servers.
- The developers were tracking users without their consent.
Why is everything such a great deal for Google? In case you haven’t read, Microsoft had previously flagged the extension as malware before. And to make matter worse, the extension came with new tracking abilities that may concern your browsing privacy. So, if you have ever installed the extension, we highly suggest taking caution and replace it with other alternative extensions.
7 Signs That Your Device Has Been Infected by Malware
Again, Google has not said a word about the removal of the extension. So, you can never really tell how the malware works or what it does. But still, we managed to compile a list of common signs that a device has been compromised by a malware entity. These are as follows:
Sign #1: Poor computer performance
Is your computer performing slower than usual? Then your device may have been infected. You may have visited a website that tricked you into installing a malicious software program. And once it runs, you experience a significant drop in performance.
Sign #2: Random infection warnings accompanied by messages that convince you to purchase a product to fix them
Unexpected warnings and windows that pop up can be a sign that your device has been infected by malware. These pop-ups may tell you that security threats exist on your computer, and they often ask you to click on a link to get rid of the threats. Legit protection software programs like Windows Defender will never show prompts with links to suspicious sites.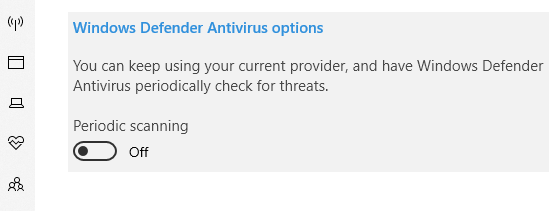
Sign #3: Random sounds
Computers that have been infected by malware entities are often programmed to respond using an audio signal. You will likely hear random warning beeps accompanied by a warning message. Sometimes, you will also hear bells and chimes, which you don’t know where they are coming from.
Sign #4: Unexplained Folder or File Changes
Are your files missing? Is the placement of your icons incorrect? These changes won’t happen unless you made them, or a virus has caused them.
Sign #5: Redirects to unknown websites
Another sign of a malware infection is when a legitimate antivirus software notifies you that an app is trying to connect to a site that you have not heard of. Technically, computers are not designed to establish their connections. These connections need to be initiated manually. If you did not establish such a connection, then a faulty application or program may be doing it for you.
Sign #6: Unable to download updates
Computer threats cannot decide for themselves. However, they are programmed to have this self-preservation instinct. And so, to get rid of them, an average computer user may use an antivirus program. Now, if you can’t install any available update, it could be caused by the malware’s design.
Sign #7: Spam messages sent from your email
Again, malware entities work in various ways. And one way they attack is by taking advantage of a victim’s social media account or email. If your computer is infected, people in your contact list will receive an email or message from you asking them to click on an infected link. Once clicked, the malware spreads to that person and onto his friend list.
How to Remove the Great Suspender Malware
Now that you know the signs that your device has been infected, what to do about the Great Suspender malware? For sure, you need to remove it.
Below are some effective ways to remove malware from Windows 10/11.
Method #1: Uninstall the Great Suspender Extension
If, by any chance, the extension is not yet disabled on Google Chrome, uninstall it manually. Uninstalling the Great Suspender extension can effectively get rid of the malware. Here’s how to do it:
- Unsuspend all the suspended tabs. To do that, click on the Great Suspender extension icon. And then, click the Unsuspend All Tabs option. Take note that if you skip this step, all your suspended tabs may be lost.
- After that, right-click on the extension’s icon and click Remove from Chrome.
- Finally, hit the Remove button on the pop-up.
Method #2: Switch to Safe Mode
One way to identify or detect critical problems caused by malware entities is by running your computer in Safe Mode. This is an alternate boot method that allows for an easier way to diagnose computer issues like malware infection. In this mode, only minimum services and programs are run.
To run your computer in Safe Mode, here’s what you should do:
- Log in to your Windows 10/11 device and click the Start button.
- Tap the Power icon and hold the Shift key.
- Select Reboot.
- In the menu that appears, select the Troubleshooting option.
- Go to Advanced Options and click Startup Settings.
- Tap the Restart button.
- Next, a window with numbered options will appear. Select Enable Safe Mode to enter into Safe Mode.
- Once your computer boots into this mode, you will notice that it will run faster. This is because there is no malware infection. However, if the issue persists, try the succeeding methods.
Method #3: Delete Temporary Files
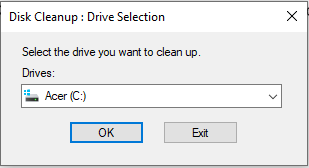
Believe it or not, deleting temporary files can remove malicious entities like the Great Suspender malware from your Windows device. To do this, you can use the in-built Disk Cleanup utility.
The Disk Cleanup utility is created by Microsoft to help remove temporary files, clean the Recycle Bin, and remove unwanted files. To use it, follow these steps:
- Navigate to the Cortana search field and type disk cleanup.

- Hit Enter.
- Once this tool opens, click the Free Up Disk Space by Cleaning Unnecessary Files option.
- You will then see a small window that pops up. In the drop-down menu, select the drive that you want to clean.
- Hit OK.
- Now, select all the files that you want to delete and hit OK.
- After that, the tool will proceed to ask for your confirmation. To agree, hit the Delete Files button.
Alternatively, you can use a third-party PC Repair tool instead. These tools are designed to identify and resolve performance problems that may be plaguing your device. They can address a wide range of system problems, improve security and privacy, optimize your device’s performance, and most importantly, clean up your drive of unwanted files.
Method #4: Remove System Restore Points
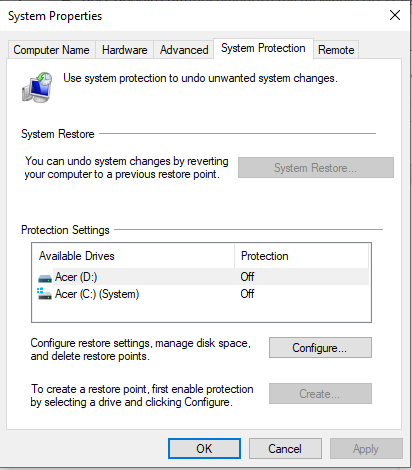
Some System Restore Points that have been generated may contain potential malware entities. So, try to delete them to ensure no traces are left on your PC.
Here is how to remove restore points that may have been contracted to the Great Suspender malware:
- Press the Windows + Break keys. This will launch the System window.

- Select System Protection.

- Next, choose the drive where system protection is saved and hit the Configure button.
- Proceed by clicking OK.
- And then, tap the Delete button to remove all restore points you have created on your system.
- Click Continue.
- Restart your computer.
Method #5: Reset Chrome’s Settings
As you already know, the Great Suspender is a browser extension. This means it could be used as a gateway for malware. And because Google has flagged it as a malware entity itself, it is probably best to reset your web browser’s settings.
To do that, do the following:
- Click the three-dotted menu and select Advanced Setting.
- Select the Reset Browser Settings option.
Method #6: Scan Your Device Using a Third-Party Antivirus Suite
Assuming you have already removed all traces of the Great Suspender malware, the next thing you should do is double-check to make sure no remnants are left. For this, you will need a third-party antivirus suite.
One software we suggest is Outbyte AVarmor. It is a trusted security software program that protects your system against malware and other threats. It scans, detects, and gets rid of malware all while offering real-time protection.
Removing malware entities can be a tedious job. So, save yourself from the hassle by using a third-party program instead.
Method #7: Use Windows Defender
Windows 10/11 comes with a built-in anti-malware software called Windows Defender. This tool is fairly easy to use. Here’s how to use it to scan for malware on your PC:
- Press the Windows button.
- Go to Settings. It is the gear-shaped icon above the Power icon.
- Select Updates and Security.
- Navigate to Windows Security and select Virus and Threat Protection.
- Lastly, click the Quick Scan button.
- Wait for the scanning process to complete.
- Restart your computer.
- You may also perform a more thorough scan. Click the Scan Options and select the best option that meets your needs.
Method #8: Recover Any Damaged Data or Software
A cybersecurity tool will tell you if a malware entity exists in your system. However, you can never tell if it has infected your device already. Thus, you may need to perform recovery methods in case any data has been damaged.
Here’s how to recover your files in Windows 10/11:
- Click the Start menu and go to the System and Security section.
- Select Backup and Restore.
- If you have created a backup, you can find it here.
- Next, click the Restore My Files option to recover your files.
- Now, select the files that you want to restore. You may choose to restore everything by clicking Browse for Folders.
- Click Next.
- Instruct Windows where you want to put your restored files.
- Select In the Original Location and hit Restore.
- If Windows finds that all the original files are still on your device, you may choose to replace them by clicking Copy and Replace.
- Once the restoration process is complete, hit the Finish button.
How to Protect Your Device from Malware
When it comes to threats like malware, prevention is always better than cure. And even if there are many types of malware entities out there, there are also various ways to protect your device from them. Check out our malware prevention tips below:
Tip #1: Update Your Operating System
Make sure your operating system is up to date. Cybercriminals and hackers are always looking to exploit vulnerabilities in outdated software. Once an update is available, install it as soon as possible.
Tip #2: Don’t Click on Suspicious Links
Did a window pop up with a link on it? Never click on it. Close the window and steer clear of the site you’re currently at. The same applies to links on emails or text messages.
Tip #3: Install Only the Important Apps
As much as possible, limit the number of apps you install on your device. It would be best to install only those that you use regularly. And if you no longer use a certain app, uninstall it.
Tip #4: Run Regular Security Scans
New malware strains are created every day. Make sure your devices are protected and prepared for them. Run regular security malware scans.
Tip #5: Check Your Emails
Beware of emails that ask for your personal information. If an email tells you to click on a link to reset your bank password, do not click on it. Rather, go to your bank’s official website and log in there.
Make sure to purchase software from reputable companies. Do not be tempted to download freeware on third-party websites as they may come bundled with malware.
Tip #7: Read Reviews Before Downloading an App
Before you download an interesting app, read reviews first. If something sounds fishy, click away.
Tip #8: Do Not Download Suspicious Email Attachments
Have you received an email that contains a suspicious attachment? Unless you know what the attachment is, do not click on it.
Tip #9: Do Not Trust Online Strangers
Social engineering is one way to deliver malware. In this method, cybercriminals use fake profiles to trick you and gain your trust. And then, you will soon be asked to provide personal details. Don’t fall for this trap.
Tip #10: Install an Ad-Blocker
Hackers use infected banners nowadays to infect devices. So, it’s safe to have a reliable ad-blocker up and running in the background at all times.
Tip #11: Be Careful While Browsing
Malware is everywhere, but it’s prevalent on sites that have poor security. If you stick to visiting reputable websites, you reduce the risk of a malware infection.
5 Alternatives to the Great Suspender Extension
Since Google has already disabled the Great Suspender extension, are you looking for a safe and secure alternative to it? Then we have got your back. In this section, we will share with you a couple of extension alternatives for managing browser tabs.
1. The Great Suspender No Tracking
Do you prefer the user interface of the Great Suspender? Then you are in luck. There is another extension that looks similar but minus the malware part. However, it’s still not available on the Chrome Web Store. So, you need to sideload it by enabling the Developer Mode first.
2. Tabby
Another simpler version of a managing tab extension is Tabby. It allows you to close older Chrome tabs when you open a new one. It comes with three different modes: Relax Mode, Focus Mode, and Customize Mode.
The Focus Mode allows you to only open five tabs at a time, while the Relax Mode allows you to open 12 tabs before it suspends the older ones. Customize Mode, on the other hand, is the default mode that allows you to open eight tabs at one time.
3. Tiny Suspender
Tiny Suspender is known for using Chrome’s native Tab Discard API. With this API, any data the user has entered on the closed tabs will stay in the browser’s memory. And if you want to open the closed tabs once again, everything will still be there.
4. The Great Discarder
This extension is similar to Tabby but more minimalist. As for Tabby, it closes a tab once you reach a certain number of active tabs. The Great Discarder, on one hand, exists any inactive tabs that have not been used for an hour.
With this extension, you may need to restore closed tabs via the History page. And in case you don’t want to close a tab, you can opt to pin it.
5. Workona Tab Manager
Unlike other tab management extensions, Workona Tab Manager follows a more productive approach to suspending Chrome tabs. If your tab count reaches 15, it suspends the whole Chrome window instead of just a series of tabs. While this can be quite annoying for some users, it is actually more productive for most.
This extension sorts all the important tabs in one place. That way, you are forced to keep on working on the more important tabs. In addition, it organizes all your bookmarks and creates different tab groups. This allows you to open all the important tabs in one click.
Key Takeaways
Malware entities should be taken seriously. The moment you detect the signs of a malware infection, you have to take action. Although we don’t know much about the Great Suspender malware and how its effects manifest, we should always stay on the safe side.
If you notice signs like poor PC performance, random infection warnings and sounds, unexplained changes in your file or folders, constant redirects to suspicious websites, spam messages coming from your email, and being unable to download updates, then be alarmed. A possible malware infection has taken place.
But fret not. You can always get rid of malware and its traces. First, uninstall any suspicious apps or extensions. And then, boot your computer in Safe Mode. Also, you can try to delete temporary files, remove system restore points, reset your browser settings, and scan your device using third-party antivirus programs.
Once you have removed the Great Suspender malware and its remnants, take preventive measures. Make it a habit to install any available updates, don’t click on any suspicious link on your email or pop-ups. Also, keep only the important apps. You can also benefit from running regular security scans and reading reviews before downloading an app.
Should you want to continue using a tab managing extension for Chrome, you can always use other alternatives, such as Workona Tab Manager, The Great Discarder, Tabby, The Great Suspender No Tracking, and Tiny Suspender.
Have you installed the Great Suspender extension before? What did you do after seeing the message by Google? We’d like to know. Share your experience in the comments.