Keyloggers are a type of spyware that records and sends out every keystroke made on a device, including sensitive information such as passwords and personal messages. This data can be used for malicious activities like identity theft and financial fraud. There are two main types of keyloggers: hardware keyloggers, which are physical devices plugged into a computer to capture keystrokes, and software keyloggers, which are programs installed on the operating system to monitor and record keystrokes.
Types of Keyloggers:
- Hardware Keyloggers: These are physical devices attached to a computer to record keystrokes, and they appear exactly as shown in the featured image.
- Software Keyloggers: Programs installed on the operating system to monitor keystrokes.
How are Keyloggers Installed? Through phishing, malicious downloads, email attachments, or physically attaching hardware devices to computers.
How Can You Detect a Keylogger on Your Computer?
Detecting a keylogger on your computer involves several steps aimed at identifying unauthorized software that tracks your keystrokes. Here’s how to approach this process on Windows and Mac computers:
For Windows Users:
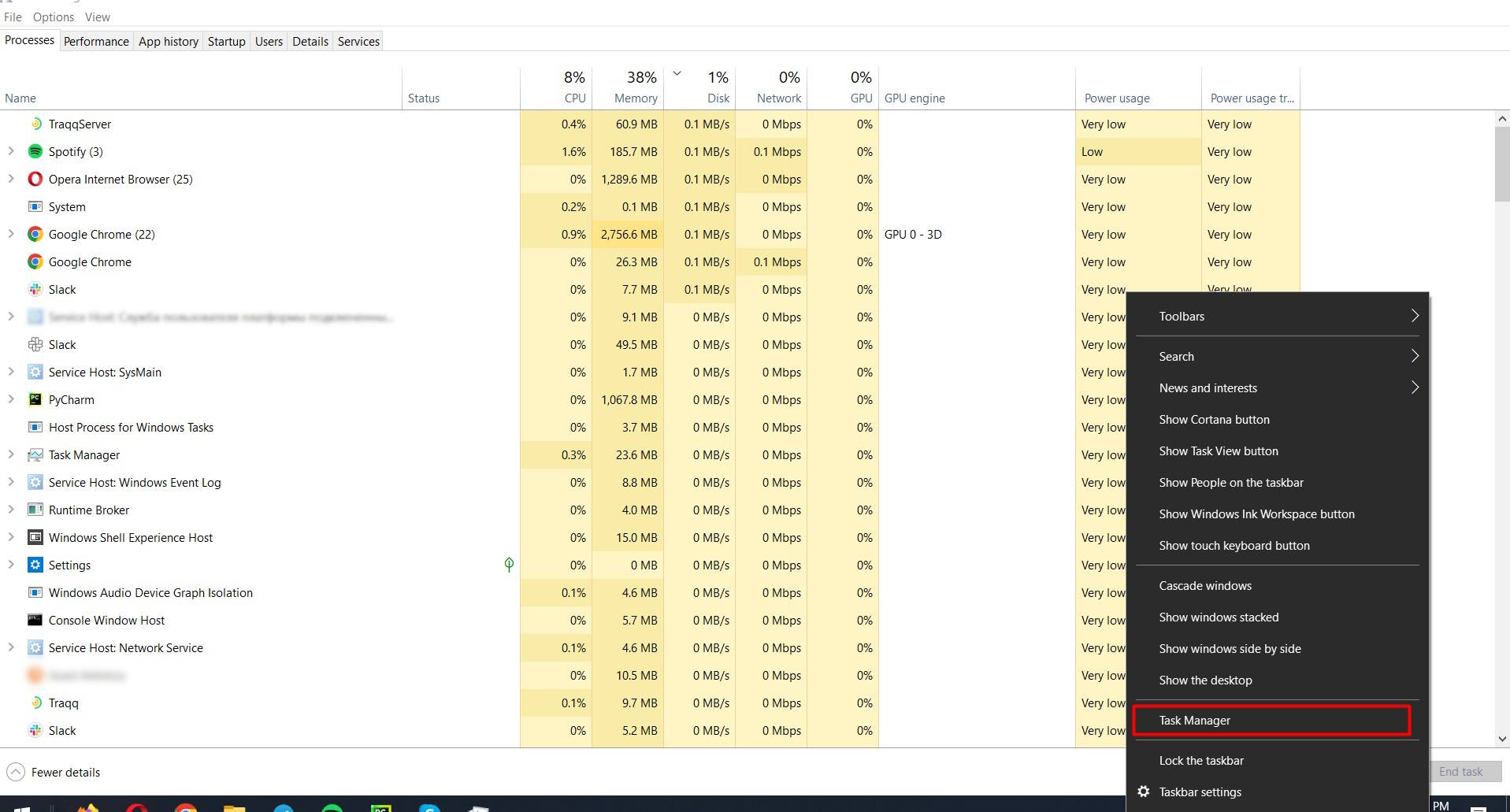
Use Task Manager:
- Access Task Manager by right-clicking the taskbar and selecting “Task Manager”.
- Expand to “More Details” to see all running processes.
- Review the list for any processes that seem unnecessary or potentially dangerous. Right-click and choose “End Task” for anything suspicious.
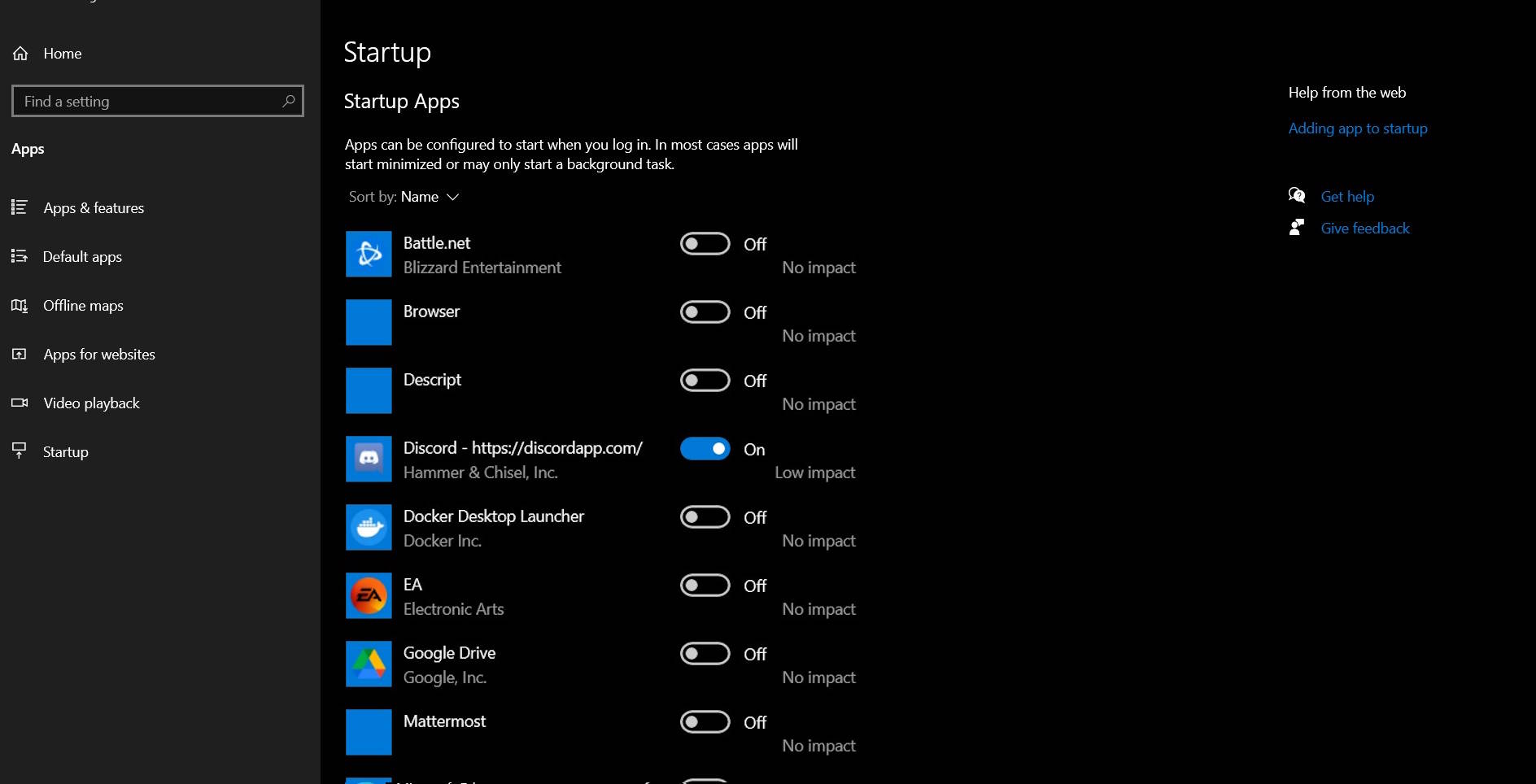
- Check the “Startup” tab for programs that automatically start with your computer. Disable any that are unnecessary or unfamiliar.
Review Installed Programs:
- Open the Control Panel and navigate to “Programs” > “Programs and Features”.
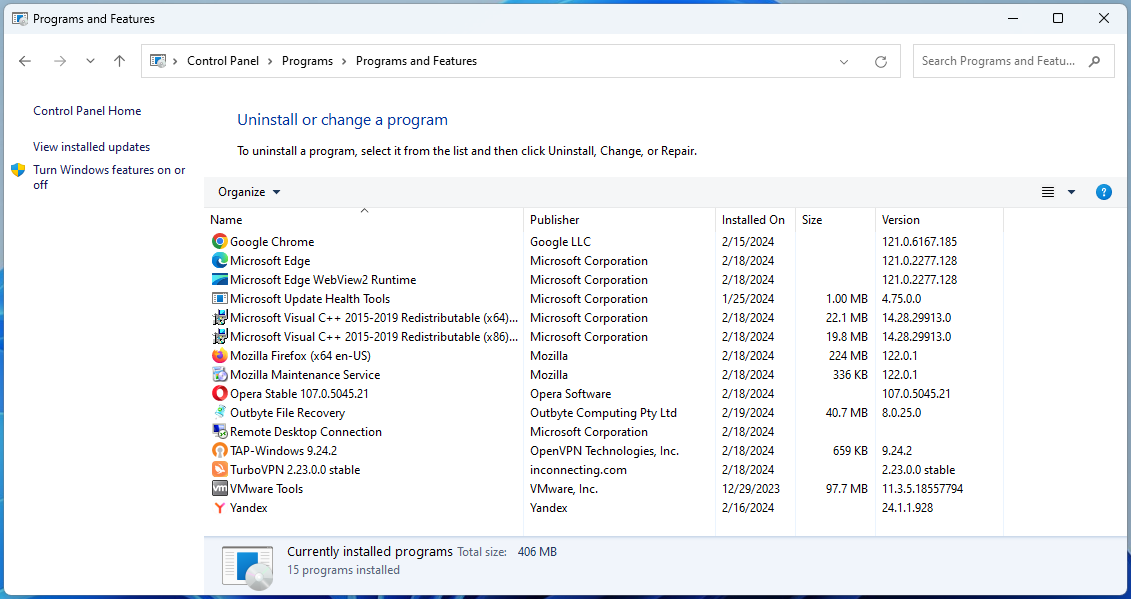
- Browse the list of installed programs for anything suspicious or unknown. If you find something unfamiliar, research it online to determine if it’s safe. Uninstall anything that’s unnecessary or potentially harmful.
For Mac Users:
Use Activity Monitor:
- Open Activity Monitor from the Utilities folder within Applications.
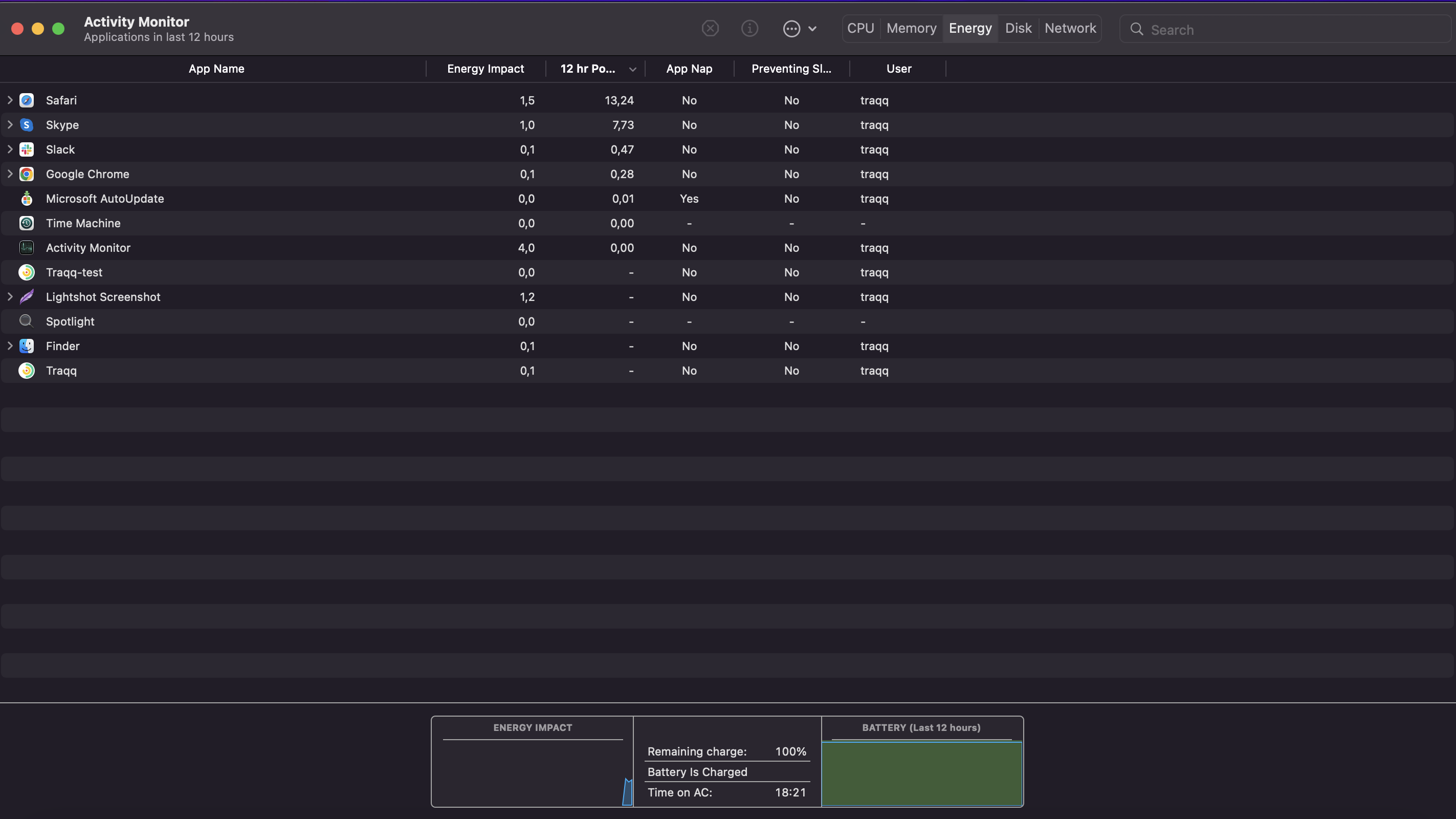
- Examine all processes for anything that doesn’t seem to belong. Use online research to determine if a process is legitimate. If something appears malicious or unnecessary, select it and click the “X” button to quit the process.
Identifying Suspicious Programs:
- On both Windows and Mac, suspicious programs might have names that seem unrelated to installed applications, use a lot of system resources without a clear reason, or are not recognizable as part of the software you intentionally installed.
Checking for Unusual System or Browser Settings Changes:
- System Settings: Be alert for any changes in your computer’s behavior or settings that you didn’t make. This can include new programs starting automatically, changes in your homepage or search engine in web browsers, or unexpected toolbars.
- Browser Extensions and Plugins: Review your browser’s extensions or plugins. Remove any that you didn’t install yourself or that seem to serve no useful purpose.
To detect and remove a keylogger, carefully monitor your system and research unfamiliar processes or programs online to determine if they are malicious.
Signs of a Keylogger Infection
Here are the common symptoms to look out for:
- A noticeable decrease in your device’s operating speed.
- Delays in typing or cursor movements.
- Applications take longer to open, or the system freezes more frequently.
Unexplained Internet Data Usage:
- Significant increase in data consumption that cannot be attributed to your known activities.
- This can indicate that the keylogger is sending captured data to an external server.
Strange Files or Applications:
- Unfamiliar files or programs on your system that you don’t remember installing.
- These could be the keylogger itself or other associated malware.
Detecting these symptoms can help in the early detection of keyloggers, allowing to protect personal information.
Can Anti-malware Tools Detect Keyloggers?
To detect keyloggers, regularly scan your system with updated anti-malware software. These tools are designed to find and eliminate malicious software, including keyloggers, protecting your sensitive information. Ensure your anti-malware is always updated to improve its effectiveness against new threats.
How Can You Manually Remove a Keylogger?
Manually removing a keylogger involves a two-step process: uninstalling suspicious programs and clearing temporary files where keyloggers might hide. Here is a structured guide for both Windows and Mac users.
Uninstalling Suspicious Programs
For Windows:
- Access Control Panel: Press the Windows key, type “control panel,” and press Enter to open the Control Panel.
- Navigate to Programs: Click on “Programs” and then “Programs and Features” to see a list of installed software.
- Identify Suspicious Programs: Look through the list for any programs you don’t recognize or seem suspicious.
- Uninstall: Right-click on the suspicious program and select “Uninstall.” Follow the prompts to complete the uninstallation process.
For Mac:
- Open Finder: Click on the Finder application.
- Go to Applications: On the sidebar, click on “Applications” to view all installed programs.
- Search for Suspicious Applications: Scroll through the applications and look for anything you didn’t install or that seems suspicious.
- Uninstall: Drag the application to the Trash, or right-click (or control-click) on the application and select “Move to Trash.”
- Empty Trash: Right-click on the Trash can icon in the dock and select “Empty Trash” to permanently remove the application.
Clearing Temporary Files
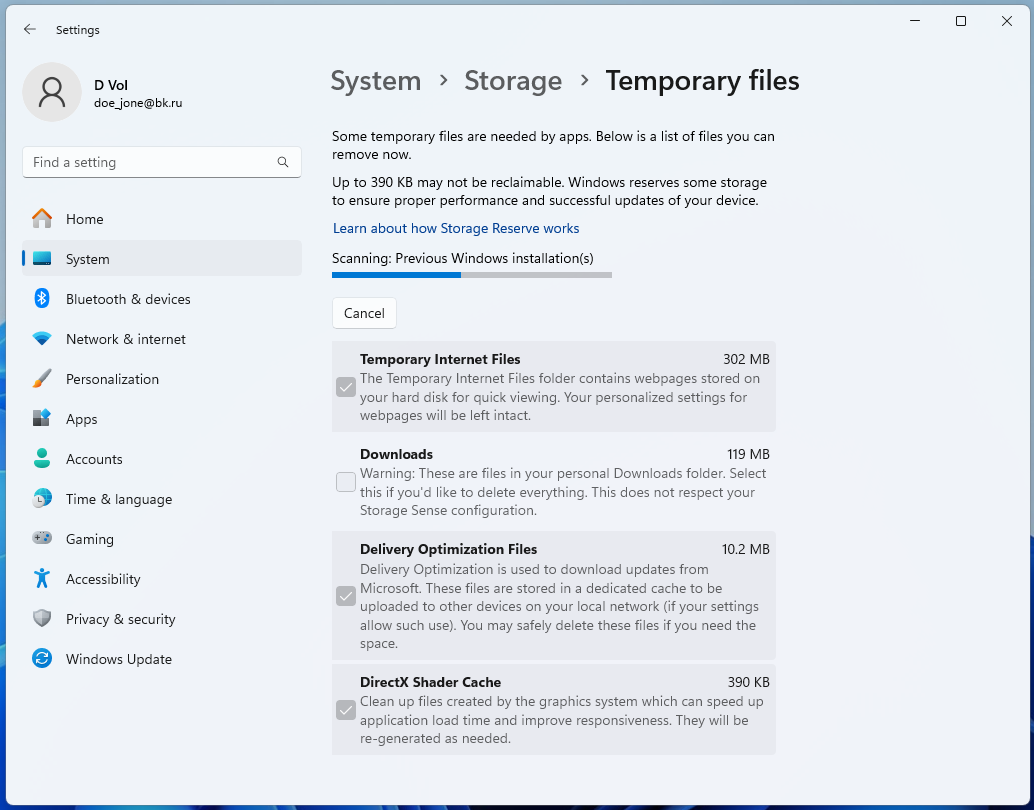
For Windows:
- Open Settings: Click the Start menu, then the cog icon to open Settings.
- Navigate to System: Click on “System,” then “Storage” on the sidebar.
- Temporary Files: Click on “Temporary files” under the “Local Disk” section.
- Select and Remove: Check the boxes for the types of temporary files you want to delete (including temporary files where keyloggers may hide) and click “Remove files.”
For Mac:
- Open Finder: Click on the Finder application.
- Go to Folder: In the Finder menu at the top of the screen, click “Go” > “Go to Folder.”
- Type Temporary Folder Path: Enter ~/Library/Caches and press Enter to navigate to the temporary files folder.
- Delete Files: Select and delete any files or folders that seem suspicious or unnecessary. Be cautious not to delete system or application files needed for your computer to run correctly.
Following these steps can help you manually remove keyloggers from your computer, but it’s always a good idea to run a scan with reliable antivirus software afterwards to ensure all malicious software has been removed.
How to Reset Your PC or Mobile Device as a Last Resort
Resetting your device to its factory settings can be an effective last resort to remove keyloggers. Before proceeding, it’s crucial to back up important data to avoid losing personal information, documents, photos, and other valuable files.
Backing Up Important Data
- For PCs and Macs: Use an external hard drive, cloud storage, or any preferred backup service to save your important files.
- For Mobile Devices (Android/iOS): Utilize cloud services like Google Drive, iCloud, or external storage solutions to back up contacts, photos, applications, and personal data.
Steps to Reset Devices
Windows:
- Open Settings: Go to the Start menu, click on the settings gear icon.
- Update & Security: Select “Update & Security” and then “Recovery” from the sidebar.
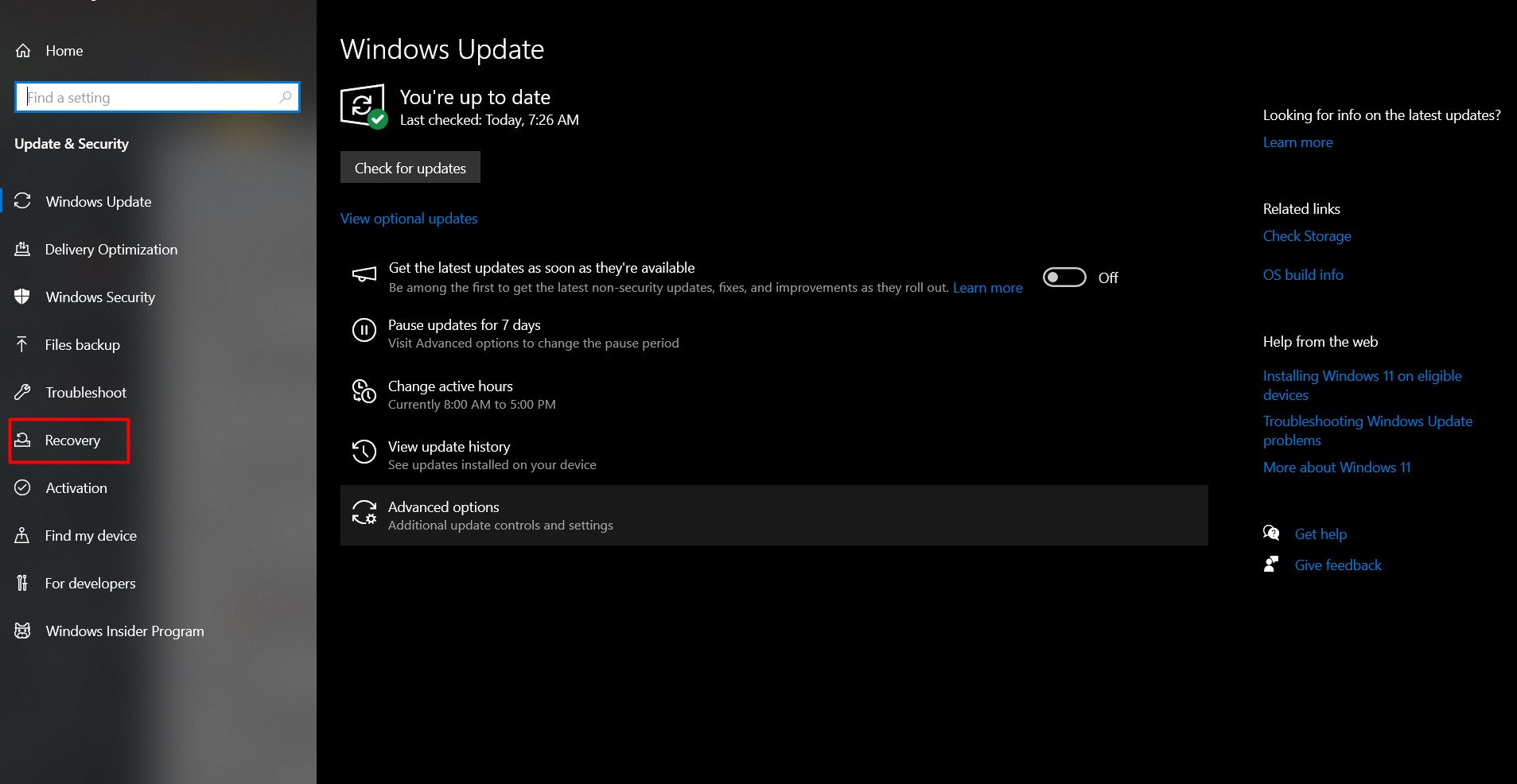
- Reset this PC: Click on “Get started” under the “Reset this PC” section.
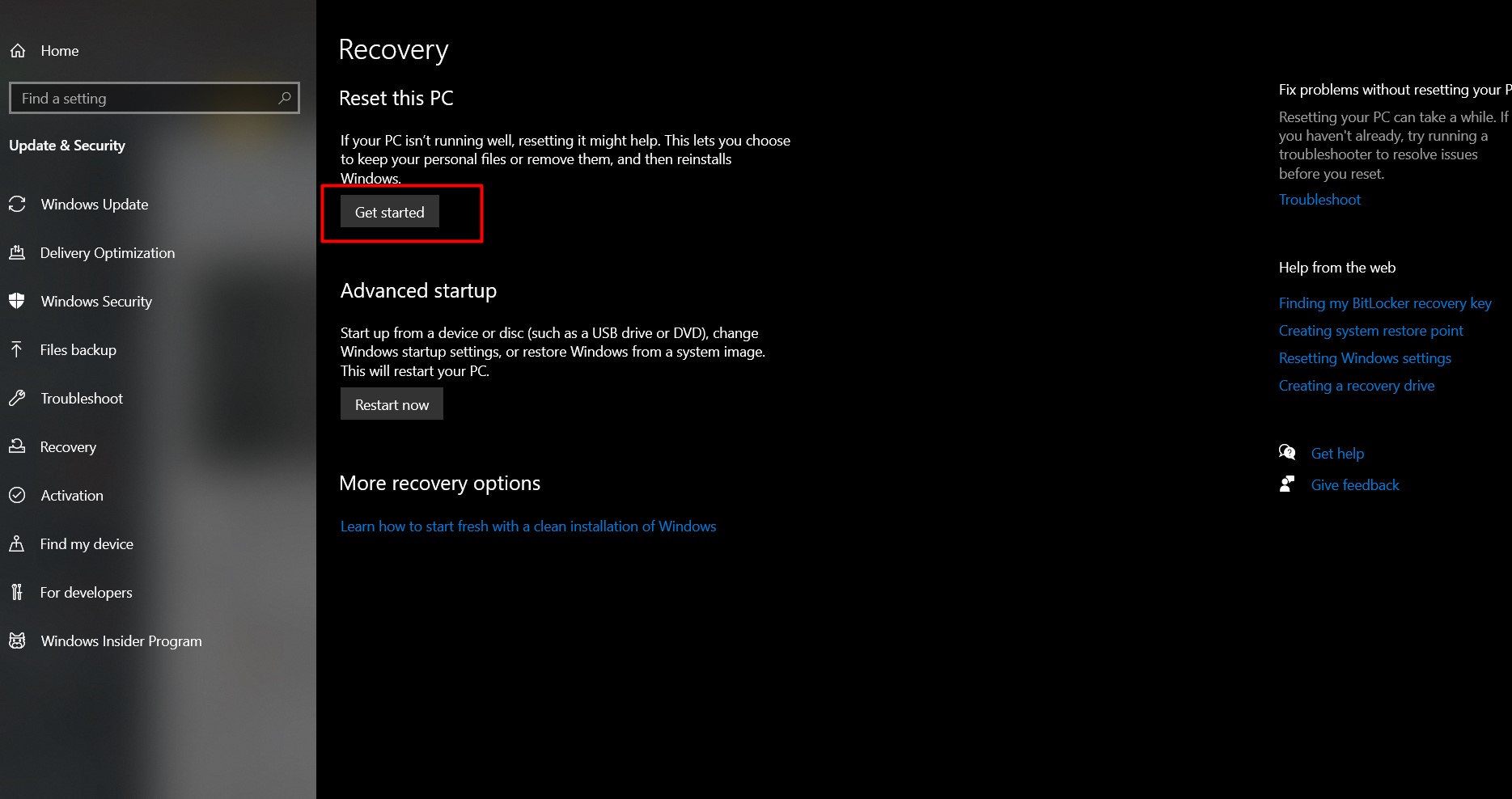
- Choose an Option: Select “Remove everything” to completely clean the device. Follow the on-screen instructions to complete the reset.
macOS:
- Restart Your Mac: Click the Apple menu and select “Restart.”
- Enter Recovery Mode: Hold down Command + R until the Apple logo appears.
- Disk Utility: In the Recovery Mode menu, open Disk Utility to erase your disk.
- Reinstall macOS: After erasing, return to the Recovery Mode menu, select “Reinstall macOS,” and follow the prompts.
Android:
- Open Settings: Navigate to the settings app on your device.
- System: Scroll down and select “System,” then “Reset options.”
- Erase All Data: Choose “Erase all data (factory reset)” and follow the prompts to complete the process.
iOS:
- Open Settings: Tap the settings icon on your home screen.
- General: Scroll down and select “General,” then “Reset.”
- Erase All Content and Settings: Tap “Erase All Content and Settings” and enter your passcode if prompted. Confirm your decision.
By following these steps, you can remove keyloggers and other malicious software from your device, restoring it to its original state. Remember to reinstall only trusted software and apps after the reset to maintain your device’s security.
How to Protect Your Device from Future Keylogger Attacks
Protecting your device from future keylogger attacks involves a multi-faceted approach that focuses on maintaining security practices and using protective software.
Keep Your Operating System and Software Up to Date
- Regularly update your operating system and installed software to get the latest security patches, which address vulnerabilities that keyloggers and malware could exploit.
Use Strong, Unique Passwords for Different Accounts
- Use strong, unique passwords for each account, combining letters, numbers, and special characters, avoiding predictable information like birthdates.
- Employ a trusted password manager to manage and securely store your passwords.
Installing Reputable Anti-virus and Anti-malware Software with Real-time Protection
- Install and maintain reputable anti-virus and anti-malware software. Choose products that offer real-time protection to help detect and prevent the installation of keyloggers and other malicious software in the first place.
- Regularly scan your device with your anti-virus and anti-malware software to detect and remove any threats. Ensure that your security software is always up to date with the latest virus definitions.
By following these recommendations, you can significantly enhance the security of your devices and reduce the risk of keylogger infections and other cyber threats.
These simple things will keep you safe:
- Education: Understand keyloggers’ entry methods and potential damage.
- Passwords: Use strong, unique passwords for all accounts.
- Software Updates: Regularly update your operating system and applications.
- Anti-Virus/Malware Protection: Install reputable anti-virus and anti-malware software offering real-time protection.
- Stay Informed: Keep up-to-date with the latest cybersecurity threats and protection strategies.
Why is Awareness About Keyloggers Important?
Risks Associated with Keyloggers
- Identity Theft: Keyloggers allow cybercriminals to capture sensitive data like usernames, passwords, and banking details, leading to identity theft. This enables fraud, unauthorized access to financial accounts, and transactions in the victim’s name.
- Financial Fraud: Keyloggers capture financial information such as credit card details and PINs, enabling cybercriminals to commit financial fraud by stealing funds or making unauthorized online purchases.
Additional Resources for Keylogger Detection and Removal
- Online forums and cybersecurity blogs are valuable resources for guidance on detecting and removing keyloggers. They offer insights into current threats and expert advice on protection against keyloggers. Engaging with these communities provides personalized support and recommendations from users with similar experiences.
- Software providers offer tools to detect and remove keyloggers, accessible through their official websites. These sites provide the latest security software and updates, equipping users with necessary protection tools.
- If self-removal of keyloggers fails, it’s advisable to seek professional help. Cybersecurity experts and computer repair services possess the expertise and tools to identify and eliminate sophisticated keyloggers, ensuring complete removal and restoring device security.
