It’s hard to go without Internet these days when the demand to be always connected is continually increasing. It has become a necessity for us always to check our emails, post updates on social media, connect with other people and catch up with work. Fortunately, you can find free Wi-Fi almost anywhere—in schools, cafes, libraries, parks, train stations, airports, etc. Public Wi-Fi networks have made it easier for us to connect to the Internet outside our home. Plus, who doesn’t want free Wi-Fi? Cellular data can be expensive. A gigabyte of cellular data can cost you $30 (AT&T), while the average data cost is $45 a month for around 4GB of LTE data. If your cellular plan doesn’t come with a massive data allowance, then free Wi-Fi is a great boon.
However, connecting to public free Wi-Fi comes with security and privacy risks. If you’re connecting to a public hotspot directly and without the protection of a VPN, you are exposing yourself to all kinds of malicious online attacks such as identity theft, data leaks, online activity monitoring, restricted browsing, computer hijacking, and other security threats.
Public WiFi Security Risks
People often think that public Wi-Fi offers the same online protection as one’s home network. This is anything but real. It might be annoying having to type in your password every time you want to connect to your home network, but it does provide you protection against online attacks. Not only does it prevent your neighbor from leeching off your Internet connection, but it also encrypts your data and shielding it from prying eyes. Here are some of the risks you might encounter when you connect to a public Wi-Fi network:
- Guest Wi-Fi networks have no password by default. This means everything that goes through it is not encrypted. Anyone with even a simple tool or script can view which websites you have been to. They can also intercept and read emails that you send, access files on your computer, and view your passwords. All public Wi-Fis are the same—whether you’re in a school library or the coffee shop around the corner.
- Even if there isn’t an attacker around, you’re still putting your privacy and security in the hands of people on that public network. You might have the latest antivirus, but malware could spread from other users on your network to your computer without you even knowing it. Fortunately, Wi-Fi snooping has become more difficult with the introduction of SSL encryption. This trend is being used by almost every website, especially the popular ones. When you see HTTPS in the web address of the website you’re visiting, it means that the website is using a secure web standard. So even if people can track the websites you’re visiting, they can’t see the email or password you used to log in. Using SSL is just one of the steps to make the Internet more secure, but it isn’t enough. In fact, anyone can bypass SSL using a single method, which we will discuss below.
- One of the most common threats to public wifi security is the HTTPS stripping attack presented by security expert Moxie Marlinspike at the Black Hat DC in 2009. The sslstrip tool hijacks HTTPS traffic on your network and redirects it to the HTTP version where the attacker can harvest your information without you even knowing it. The risk comes from the fact that most people don’t necessarily type in https:// when they’re visiting a website. So when they first visit the site, they go to the HTTP version. What most websites do is redirect the user from the HTTP site to the HTTPS version. What sslstrip does is that it interrupts the redirection, and sends the user back to HTTP instead. The attacker can then view all your information in plain sight. Using sslstrip is a bit tricky because the hacker needs to install Python and the python “twisted-web” module for this to work. However, tools like Wi-Fi Pineapple has made stealing information on public Wi-Fi easier. Wi-Fi Pineapple is a nifty little tool created by Hak5 in 2008. The tool was initially designed for penetration testers, or “pen testers” to expose vulnerabilities of a network. The device has become popular, not only for pen testers but also for hackers as well because it has made data theft easier. In just a few clicks, the hacker can pretend to be a public Wi-Fi network, routing the user through them instead of the legitimate router. From there, the hacker can force the user to visit any website populated with malware and keyloggers, and as a result, the perpetrators can steal information or hijack the computer and ask for a ransom. Worse, it is straightforward to use that even kids can do it.
Sometimes, hackers don’t even need technical knowledge or experience to access your information. For example, if you connect to a hotel Wi-Fi network and forgot to change your Windows sharing settings, it is possible for anybody on the network to access your shared files—no hacking needed. And if your shared files are not even password-protected, you’re just making it easier for other people to see your shared files.
In 2010, a Firefox extension called Firesheep was released to demonstrate the risk of session hijacking for users of websites that only encrypt the login process, not the cookies created during login. Fire sheep intercepts unencrypted login session cookies from websites like Facebook and Twitter, then use the cookie to get the identity of the user. The collected identities of the victims are then displayed in the sidebar of the browser, and all the attacker needs to do is click the name, and the victim’s session will automatically be taken over by the hacker.
Other tools even let you do this on an Android phone or other mobile devices. One common trick is setting up a fake network, also called honeypot, to bait users. To ordinary users, the network doesn’t look out of place or suspicious because they are named similar to legitimate networks. For example, you might encounter Starbucks Wi-Fi or some other Wi-Fi networks named after the establishment or business in the area. However, these honeypots are owned and are being monitored by hackers.
Hotel Hotspot
It is never a good idea to connect to Wi-Fi networks in hotels because they are vulnerable to attacks. These networks often have many users connected to the network and hackers can just stay inside any of the rooms while harvesting information from unsuspecting hotel visitors. Plus, most hotels don’t really invest in proper security, which means that most hotels are equipped with the same hardware.
One particular incident in 2015 found that 277 hotels all over the world are vulnerable to attacks. These hotels were using ANTlabs’ InGate device to set up guest Wi-Fi networks. However, this device turned out to be vulnerable to hackers and allowed them to access users’ information, particularly credit card details held by the hotel.
Fortunately, the threat has been addressed by ANTlab by releasing a security patch to update the device’s software. However, the patch has to be installed manually, and there’s no telling whether the hotel you’ve checked into has fixed this vulnerability. Lesson learned: don’t trust hotel Wi-Fi networks.
This advice is particularly helpful for business executives who are often traveling for meetings, conferences or other business events. It doesn’t hurt to be extra cautious. In 2014, a successful security firm Kaspersky Lab found out that hackers are running a malware named DarkHotel, which targets business executives staying in hotels in Asia. The malware is spear-phishing spyware that selectively attacks business leaders staying in the hotel. And DarkHotel does this by spying through the hotel’s public Wi-Fi network. When the visitor logs into the Wi-Fi network, a page pops up and asks them to download the latest version of Messenger, Flash Player or other software. The malware then piggybacks on the installed software, stealing sensitive data from business executives.
WiFi Protector for Business Network
Wi-Fi networks owned by businesses and companies are also rich targets for hackers. Though most businesses invest in data security, guest Wi-Fi is often left open and unprotected. This leaves clients, visitors, and employees at risk. Unfortunately, there are not that many solutions that would provide sufficient network encryption to guest Wi-Fi.
Because the network is not encrypted, the users are vulnerable to threats, such as man-in-the-middle attacks, Internet snooping, password theft, malware infection, among others. Although some routers try to minimize the risks by setting up a portal page, this often leads to other problems.
Some routers, such as Linksys and Belkin, use HTTP instead of HTTPS, opening its users to various risks. This also means that anyone snooping Wi-Fi traffic can view your password when it is typed in.
Also, some guest Wi-Fi networks are still guilty of using WEP or Wired Equivalent Privacy, which is outdated and can be easily bypassed. The newer versions, WPA and WPA2, provide more protection than their predecessor.
How to Stay Safe on Public Wi-Fi
We’re not saying that it’s entirely unsafe to connect to public Wi-Fi networks or guest networks. These free Wi-Fi networks could get handy when you ran out of cellular data or when you’re out and need to check email or something. There are many ways to improve public Wi-Fi security so that you don’t have to worry about getting your information leaked or stolen. Here are some of them:
1. Check the network you are connecting to.
When you’re in a hotel or in a coffee shop, ask the staff which network you should connect to. It is easy for attackers to create a honeypot such us “Coffee Shop Wi-Fi” or “Hotel Wi-Fi” to trick visitors into connecting with this fake network and steal your data.
2. Check your sharing settings.
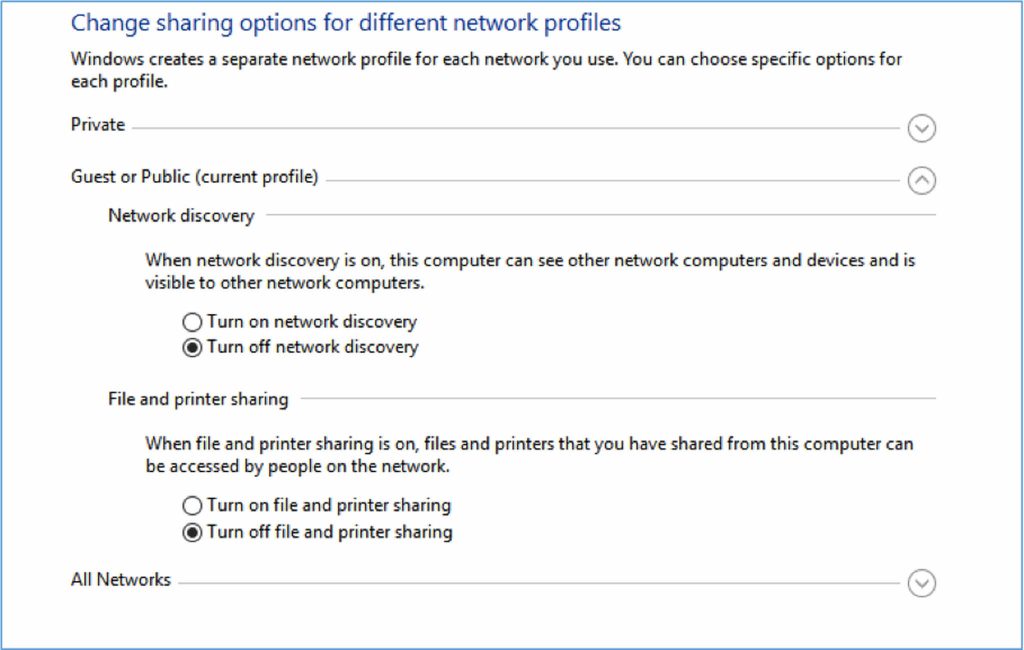
Users often forget to set this up and become unknowing victims to hackers. To check your sharing settings on Windows, go to Settings > Network and Internet > Sharing options. Click Turn off network discovery and Turn off file and printer sharing to prevent other people from accessing your files or computer.
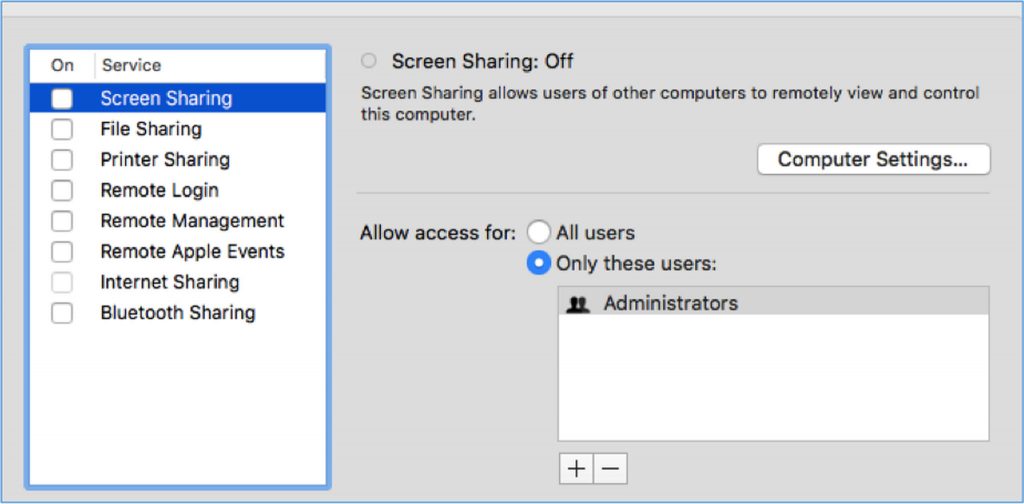
If you’re using Mac, go to System Preferences > Sharing and uncheck the items that you do not want to share to your network.
3. Enable Firewall.
You should also keep your Firewall enabled for added protection. Some users disable this setting because of apps or software asking for permissions. Although it might seem annoying at times, keeping your Firewall turned on helps deter attackers from poking around in your computer.
If you’re using Windows 10/11, go to Settings > Update & Security > Windows Security > Firewall & network protection. Next, make sure that firewall is turned on for Domain Network, Private Network, and Public Network.
For Mac users, go to System Preferences > Security & Privacy, then click the Firewall tab. Click the gold lock at the bottom left of the window to make changes to your Firewall settings.
4. Keep your operating system and applications updated.
This is a must, especially for browsers, extensions, and plugins like Flash and Java. Most malware trick users into updating these plugins so if yours is updated, you won’t fall for their ploy anymore.
5. Use HTTPS instead of HTTP.
When browsing a website, make sure you go to the HTTPS version instead of the HTTP. If the browser does not automatically redirect you to the HTTPS version of the site, there must be something going on behind the scene, so just directly type HTTPS in the address bar. For websites that you visit frequently, you can bookmark the HTTPS version of the site, so you don’t fall victim to sslstrip hackers. You can also install extensions like HTTPS Everywhere that will force browsers like Safari, Chrome, Opera and Firefox to redirect to HTTPS and use SSL encryption on all web pages.
6. Enable two-factor authentication.
Most websites like Gmail, Facebook, and online banking sites are now equipped with two-factor authentication features. It either sends a time-sensitive code, number or phrase that you need to type to proceed with your login. The code is sent via email, text message or through a mobile app. So when someone logs into your account from a location or a device you have not used before, the website will alert you of the login and you need to confirm the login using the code sent to you.
7. Do not visit sensitive websites on a public Wi-Fi network.
If possible, don’t do your online shopping or online banking activities using a public Wi-Fi network to avoid security issues. If you need to access Paypal or you need to pay bills using your online bank account, do it in a private network. You can never be really safe when it comes to free Wi-Fi so when you’re done browsing, disconnect from Wi-Fi or turn off your device. The longer your device is connected to the network, the more chances the attacker has to find vulnerabilities.
8. Invest in the best VPN for public WiFi.
To improve online safety, it is essential to invest in a good VPN client like Outbyte VPN. There are many VPNs out there, but the best VPN for public WiFi should be secure and does not keep a log of your activities.
How to Improve Public WiFi Security with VPN
A virtual private network or VPN allows you to connect to a secure server over the Internet. All your connection goes through that server, and everything is encrypted heavily to prevent snooping. Even if you connect to a public Wi-Fi network, all the hackers will see is a bunch of random characters that they won’t be able to decipher. Trying to bypass VPN is practically impossible.
When you use a VPN, your computer creates a digital tunnel through which your data is sent. These pieces of data that you send over the Internet are called packets, and each packet includes a part of your data. Each packet also contains the protocol you are using and your IP address. So when you connect to the Internet via VPN, these packets are sent inside another packet. The outer packet provides security for your data and keeps your information safe from malicious hackers.
Aside from this, the VPN’s encryption adds another layer of protection to your data. The level of encryption is determined by the security protocol employed by the VPN client. Using the best VPN for public WiFi is important to make sure that your VPN uses the most secure encryption for your Internet connection. These are some of the commonly used encryption protocols VPN providers often use.
- PPTP or Point-to-Point Tunnel Protocol. This protocol is supported by most VPN companies, but has become obsolete and no longer secure over the years. It does not encrypt your connection but instead creates a GRE or Generic Routing Encapsulation tunnel between the client and the server. The GRE tunnel encapsulates your connection, protecting your data from prying eyes. However, the encapsulation process usually results in poor performance and slow speed, especially if there’s not enough bandwidth available.
- L2TP/IPSec or Layer 2 Tunnel Protocol. L2TP is an upgrade of PPTP, with the added protection IPSec for encryption. It offers a high level of security and is supported by most VPN providers.
- SSTP or Secure Socket Tunnel Protocol. This is a new protocol that uses SSLv3/TLS for encryption. This means that SSTP can pass through most firewalls and proxy servers by using TCP port 443 or HTTPS.
- OpenVPN. This is one of the latest and most secure VPN clients supported by significant VPN providers. It is maintained by the open-source community and uses OpenSSL for encryption. OpenVPN uses UDP and TCP protocols for speed and performance.
Benefits of Using Best VPN for Public WiFi
Aside from acting as a WiFi protector, VPN also has many benefits that some users are not aware of. Here are some of them:
- Bypass content restrictions. By tunneling your connection through secure servers, VPN allows you to unlock restricted content. For example, you will be able to access websites that are blocked, including social media and video streaming sites, even when you’re connected to a guest Wi-Fi network. You can also access geo-restricted content through VPN. So if you want to watch Netflix USA from other parts of the world, all you have to do is connect through VPN, and your IP address will be masked to show that you are located in the same area. You will then be able to view content that is limited to that area, in this case, the US.
- Anonymous browsing. Whenever you connect to the Internet, you always leave a digital trail that can be traced back to you. For example, when you visit a website, your IP address and other information are logged by the website you are visiting. When you use VPN, your identity is masked because your information is encrypted. Even your Internet provider won’t be able to spy on you.
- Fast Internet connection. Most ISPs throttle Internet connection when they detect that you are using up too much data. Online gaming and video streaming are the main culprits that cause internet throttling and sometimes, even blockage. VPN hides your online activities so that ISPs won’t be able to monitor you, hence avoiding throttling of your Internet connection.
However, keep in mind that the degree of protection and performance of your VPN gives you depends on the protocol being used, the location of the server, and the amount of traffic that goes through the server. Many companies offer free VPN but do your research because you might only be disappointed in the end. Aside from adds, free VPN apps are subject to limited bandwidth and data caps. For a 100% secure and reliable connection, it is better to invest in a paid VPN service – for your security and peace of mind.
