Encryption assists in securing data that you transmit, receive, and store on a computer. This includes text messages on your mobile, emails, and banking details submitted via your online account.
Easy and cheap access to the Internet has made it possible to read articles, access social media, do shopping online, and more. When you buy anything from an online store, you provide your name and email address and your sensitive information like banking details, passwords, etc.
It is incredibly convenient to purchase and trade products online while relaxing at your home. Safety is a serious issue on the Internet, mainly when you use it to transfer confidential data. The most reliable method to protect online information is to use encryption. Please continue reading to know in detail about encryption and its working.
Encryption, and how it works?

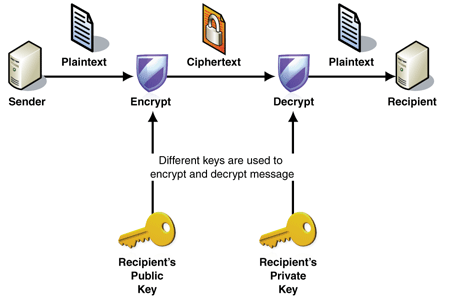
Encryption is a method of encoding a document or a file, ensuring that the intended individuals can only read it. Encryption utilizes an algorithm to cipher or encode information and then requires the recipient party’s key to decipher, or decode, data. The information in a non-ciphered text is plaintext info that anyone who intercepts the data can easily read. When encryption is applied to the plaintext, it becomes a ciphered text that can only be read by the individuals having the appropriate key for decryption.
Encryption uses a set of algorithms to cipher and deciphers the data with a pair of matching keys. Even if cybercriminals get access to the encrypted information, they can’t read the data unless they have access to the key needed to decrypt it.
Symmetric and Asymmetric Encryption
Encryption has two different types – symmetric and asymmetric encryption.
- Symmetric Encryption – It utilizes a single key to encrypt and decrypt the data.
- Asymmetric Encryption – In this type of encryption, two different keys – public and private – are used for data encryption and decryption. Public keys are made accessible to the users for encryption, while a private key is used for decoding and then sending back information in encrypted form to the users.

Types of symmetric encryption
Symmetric encryption uses one key to encode the data, and the same key is used to decode the information. Here are the main types of symmetric encryption algorithm:
1. DES
Data Encryption Standard is known to be a low-level encryption method. It utilizes 56-bits of a 64-bit key to encode information in fixed data blocks. Due to technological advancements and a decline in hardware costs, DES has become obsolete for personal information security.
2. AES
Advanced encryption standard is a widely used symmetric encryption method. It has overcome the security issues that were not handled by DES. It uses a block length of 128-bits for data encryption and may have various key lengths, based on the complexity of encryption desired.
3. RC2
Rivest cipher came as a replacement for DES in 1980. It encodes the messages in 64-bit blocks but has different key sizes, ranging between 8-128 bits.
Types of asymmetric encryption
Asymmetric encryption functions somewhat differently from symmetric encryption. Anyone with a public key will be able to encode data after providing authentication. However, only the individual in charge of a private key will be eligible to decode it. RSA and ECC are the most popular kinds of asymmetric encryption algorithms in use:
1. RSA
RSA is the mostly applied asymmetric algorithm for encryption and decryption. The strength rests in the “prime factorization” process on which it depends. Practically, this approach requires two big arbitrary prime numbers, and these numbers are multiplied to produce another large number. The challenge here for cybercriminals is to evaluate the actual prime number of this vast, multiplied number to access the private key, which turns out to be a herculean task and thus makes RSA safe for its intended use.
2. ECC
Elliptic Curve Cryptography (ECC) is an asymmetric encryption algorithm that was first introduced in 2004. In ECC, a number denotes a value on the graph is multiplied by a particular integer giving another point on the curve. Now to break this puzzle, you need to find out the two chosen spots on the curve. ECC mathematics is designed so that it is nearly impossible to specify the second point, even though you know the initial point.
SSL and encryption
Mostly used security protocol, known as SSL or “Secure Sockets Layer,” utilizes an asymmetric encryption method to safeguard the data transmission between the browser and a website. Here, the public key is made accessible to all the site visitors while the private key is kept hidden by the server. A website with a valid SSL certificate has a padlock sign on the left of the browser. It uses HTTPS (Hyper Text Transport Layer Secure) instead of plain old HTTP for internet communication – meaning your data will remain safe from the reach of hackers on this site.
Almost all the websites and especially those dealing with confidential information (such as usernames, passwords, credit card or banking details) of the customers use SSL to protect their site and user’s information from all known cybersecurity risks. Suppose you do not activate an SSL certificate on your website. In that case, it becomes vulnerable to cyber-attacks, and the hackers can quickly get their hands on the information being shared in plaintext form.
Benefits of Encryption
Here are the significant advantages of utilizing encryption:
1. Complete data security
A full encryption approach offers peace of mind for companies and their customers since it safeguards the information in all conditions – both at rest and in motion.
2. Protection across numerous devices
Data encryption program guarantees that all information on any device is fully secured with the same security in place that you find in the data stored on a personal computer.
3. Data integrity
Encryption helps keep the information secure from modification, and if any alteration is made with the data, the users can figure out that it has been tampered with.
Conclusion
Encryption has now become crucial for all businesses to secure their website resources and user’s sensitive data. Online stores use SSL certificates as an encryption method to protect their confidential information to keep the attackers at bay. It is nearly impossible for cybercriminals to understand the encrypted information shared between the user and the server. This makes encryption an effective way of protection against data breaches.

