Phobos is a ransomware type of malware that encrypts a user’s file using the AES 256-bit encryption standard. After which, it demands that the victim’s part with a ransom amount that has to be paid in Bitcoins.
Phobos was first spotted in 2019 and is attributed to the same hacker group that is responsible for the Dharma ransomware. It is mostly distributed via hacked remote desktop connections.
Phobos encrypts a variety of files, including executable. Normally, the encrypted files also have the email of the attacker added. The general pattern of the encryption is: <original name>.id[<victim ID>-<version ID>][<attacker’s e-mail>].<added extension>.
What Can the Phobos Malware Virus Do?
Just like Dharma, Phobos infects computers by exploiting poorly secured RDP ports to infiltrate networks and execute a ransomware attack.
After encrypting the files with a .phobos extension, the ransomware will then request that a ransom amount be paid in Bitcoins to a dark web address that is shared via a readme.txt document. Some victims of the malware have been asked to pay as much as $3000 for the chance to get their files back.
Before the encryption is executed, the malware entity kills processes that could block access to the files that are targeted for encryption. The following is a full list of the processes that are killed:
- msftesql.exe
- sqlagent.exe
- sqlbrowser.exe
- sqlservr.exe
- sqlwriter.exeoracle.exe
- ocssd.exe
- dbsnmp.exe
- synctime.exe
- agntsvc.exe
- mydesktopqos.exe
- isqlplussvc.exe
- xfssvccon.exe
- mydesktopservice.exe
- ocautoupds.exe
- agntsvc.exe
- agntsvc.exe
- agntsvc.exe
- encsvc.exe
- firefoxconfig.exe
- tbirdconfig.exe
- ocomm.exe
- mysqld.exe
- mysqld-nt.exe
- mysqld-opt.exe
- dbeng50.exe
- sqbcoreservice.exe
- excel.exe
- infopath.exe
- msaccess.exe
- mspub.exe
- onenote.exe
- outlook.exe
- powerpnt.exe
- steam.exe
- thebat.exe
- thebat64.exe
- thunderbird.exe
- visio.exe
- winword.exe
- wordpad.exe
The following image shows a fragment of the Phobos malware code and how it directs the killing process: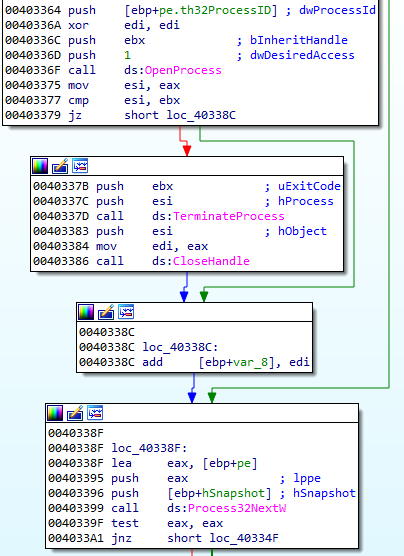
One of the reasons that cybercriminals are able to tell that Dharma and the Phobos malware entities are created by the same group despite having different code is the fact that they share the same ransom note. The typeface and the text are the same.
How to Remove the Phobos Malware
The best way to deal with the Phobos malware is to deploy an anti-malware solution and to refrain from contacting the cybercriminals. It is true that paying the ransom might save you the pain of losing your files, but it is not an ideal solution.
Cybercriminals cannot be trusted to deliver the decryption keys and even if they could, it makes it more likely that they will attack in the future as you and the others who choose to pay, encourage them to do so.
Anti-malware solutions have been found to be more effective against viruses when the computer is on Safe Mode. This is because Safe Mode only operates a minimum of Windows apps and settings, and therefore commits more computing resources to the hunting down of the malware entity.
The Phobos ransomware is also known to use several persistent processes, such as installing itself in the %APPDATA% and Startup folder, where it adds startup registry keys to autostart. On Safe Mode, the autostart items are disabled.
Another piece of software that you might need as you battle the Phobos malware is a PC repair tool. It will both clean your computer and repair broken registry entries.
How to Protect Your Computer from the Phobos Malware
As part of this Phobos malware removal guide, we shall also share with you a few tips on how to avoid an infection by the ransomware. The Phobos ransomware mostly targets corporate entities that use Remote Desktop Protocol (RDP) access. Thus, businesses can review where the RDP has been enabled and either disable or make certain that credentials are strong enough that brute force attacks cannot happen. For this, we recommend using two-factor authentication.
At the same time, businesses need to agree on a common cybersecurity strategy for everyone because that way, it is easier to mitigate risks.
