If you think that your Mac is secure from malware, think again. Malware authors have become adept at exploiting vulnerabilities of various platforms, including macOS. This is evident in the previous malware infections that targeted Macs, including the Shlayer malware and the Top Results malware.
What Is Silver Sparrow macOS Malware?
Recently, Red Canary, Malwarebytes, and VMware Carbon Black security researchers have discovered a new macOS malware that infected more than 40,000 Macs globally. This new threat is named Silver Sparrow. According to Malwarebytes, the malware has spread across 153 countries, with the United States, the United Kingdom, Canada, France, and Germany with the highest concentrations. It is unclear how many of these 40,000 are M1 Macs and we do not know exactly what the distribution looks like.
Researchers have noted that even though Silver Sparrow poses a reasonably serious threat to the infected device, it exhibits no malicious behavior that is often expected from common macOS adware. This makes the malware more baffling because security experts have no idea what the malware was designed to do.
However, researchers noticed that the malicious software remained ready to deliver a malicious payload anytime. Upon investigation, the Silver Sparrow macOS malware strain has never delivered a malicious payload on the infected devices, but they warned the affected Mac users that it still poses significant risks despite its dormant behavior.
Though researchers have not observed Silver Sparrow delivering additional malicious payloads, its M1 chip compatibility, global reach, high infection rate, and operational maturity makes the Silver Sparrow a reasonably serious threat. The security experts also discovered that the Mac malware is compatible with both Intel and Apple Silicon processors.
Here’s a rough timeline of the evolution of the Silver Sparrow malware:
- August 18, 2020: Malware version 1 (non-M1 version) callback domain api.mobiletraits[.]com created
- August 31, 2020: Malware version 1 (non-M1 version) submitted to VirusTotal
- September 2, 2020: version.json file seen during malware version 2 execution submitted to VirusTotal
- December 5, 2020: Malware version 2 (M1 version) callback domain created api.specialattributes[.]com created
- January 22, 2021: PKG file version 2 (containing a M1 binary) submitted to VirusTotal
- January 26, 2021: Red Canary detects Silver Sparrow malware version 1
- February 9, 2021: Red Canary detects Silver Sparrow malware version 2 (M1 version)
What Does the Silver Sparrow Malware Do?

Security firm Red Canary discovered the new malware, which targets Macs equipped with the new M1 processors. The malware is named Silver Sparrow, and uses the macOS Installer Javascript API to execute commands. Here’s what you need to know.
Nobody knows for sure. Once on a Mac Silver Sparrow connects to a server once an hour. Security researchers are concerned that it could be gearing up for a major attack.
Security company Red Canary believes that, while Silver Sparrow has now yet delivered a malicious payload, it could pose a fairly serious threat.
The malware has become notable because it runs on Apple’s M1 chip. That doesn’t necessarily indicate that the criminals are specifically targeting M1 Macs, rather it suggests that both M1 Macs and Intel Macs can be infected.
What is known is that the infected computers contact a server once an hour, so it may be some form of preparation for a major attack.
The malware uses the Mac OS Installer Javascript API to execute commands.
The security company has been so far unable to determine how the commands lead to anything further, and it’s thus still unknown to what extent Silver Sparrow poses a threat. The security company nevertheless believes that the malware is serious.
On the Apple side, the company has revoked the certificate used to sign the package associated with the Silver Sparrow malware.
Despite Apple’s notary service, macOS malware developers have successfully targeted apple products, including those using the latest ARM chip like MacBook Pro, MacBook Air, and Mac Mini.
Apple claims to have an “industry-leading” user protection mechanism in place but the malware threat keeps resurfacing.
Indeed, it seems that threat actors are already ahead of the game, targeting the M1 chips in their infancy. This is despite many legitimate developers having not ported their applications to the new platform.
Silver Sparrow macOS malware ships binaries for Intel and ARM, uses AWS and Akamai CDN
The researchers explained Silver Sparrow’s operations in the “Clipping Silver Sparrow’s wings: Outing macOS malware before it takes flight” blog post.
The new piece of malware exists in two binaries, Mach-object format targeting Intel x86_64 processors and Mach-O binary designed for the M1 Macs.
The macOS malware is installed through Apple installer packages named “update.pkg” or “updater.pkg.”
The archives include JavaScript code that runs before the install script executes, prompting the user to allow a program “determine if the software can be installed.”
If the user accepts, the JavaScript code installs a script named verx.sh. Aborting the installation process at this point is futile because the system is already infected, according to Malwarebytes.
Once installed, the script contacts a command and control server every hour, checking for commands or binaries to execute.
The command and control center runs on Amazon Web Services (AWS) and Akamai content delivery networks (CDN) infrastructure. The researchers said the use of cloud infrastructure makes it harder to block the virus.
Surprisingly, the researchers did not detect the deployment of the final payload, thus making the ultimate goal of the malware a mystery.
They noted that perhaps the malware was waiting for certain conditions to be met. Similarly, it could possibly detect being monitored by the security researchers, thus avoiding deploying the malicious payload.
When executed, the Intel x86_64 binaries print “Hello World” while the Mach-O binaries display “You did it!”
The researchers named them “bystander binaries” because they did not exhibit any malicious behavior. Additionally, the macOS malware has a mechanism to remove itself, adding to its stealth capabilities.
However, they noted that the self-remove feature was never used on any of the infected devices. The malware also searches for the source URL it was downloaded from after installation. They argued that the malware developers wished to track which distribution channel was the most effective.
The researchers could not figure out how the malware was delivered but possible distribution channels include fake flash updates, pirated software, malicious ads, or legitimate apps.
Cybercriminals define the rules of their attacks, and it’s up to us to defend against their tactics, even when those tactics aren’t completely clear. That’s the situation with Silver Sparrow, the newly identified malware targeting macOS. At present, it doesn’t appear to do too terribly much, but it can provide insights into tactics that we should be defending against.
Technical Specs of the Silver Sparrow Malware

According to the researchers’ investigation, there are two versions of the Silver Sparrow malware, referred to as “version 1” and “version 2”.
Malware version 1
- File name: updater.pkg (installer package for v1)
- MD5: 30c9bc7d40454e501c358f77449071aa
Malware version 2
- File name: update.pkg (installer package for v2)
- MD5: fdd6fb2b1dfe07b0e57d4cbfef9c8149
Aside from the change in download URLs and script comments, the two malware versions had only one major difference. The first version involved a Mach-O binary compiled for Intel x86_64 architecture only while the second version included a Mach-O binary compiled for both Intel x86_64 and M1 ARM64 architectures. This is important because the M1 ARM64 architecture is new and there have been very few threats discovered for the new platform.
The Mach-O compiled binaries don’t seem to be doing anything so they are called “bystander binaries.”
How Is Silver Sparrow Distributed?
Based on reports, a lot of macOS threats are distributed through malicious advertisements as single, self-contained installers in PKG or DMG form, masquerading as a legitimate application—such as Adobe Flash Player—or as updates. In this case, however, the attackers distributed the malware in two distinct packages: the updater.pkg and update.pkg. Both versions use the same techniques to execute, differing only in the compilation of the bystander binary.
One unique thing about Silver Sparrow is that its installer packages leverage the macOS Installer JavaScript API to execute suspicious commands. While some legitimate software are also doing this, this is the first time this is done by malware. This is a deviation from behavior we usually observe in malicious macOS installers, which generally use preinstall or postinstall scripts to execute commands . In preinstall and postinstall cases, the installation generates a particular telemetry pattern that looks like the following:
- Parent process: package_script_service
- Process: bash, zsh, sh, Python, or another interpreter
- Command line: contains preinstall or postinstall
This telemetry pattern isn’t a particularly high-fidelity indicator of maliciousness on its own because even legitimate software uses the scripts, but it does reliably identify installers using preinstall and postinstall scripts in general. Silver Sparrow differs from what we expect to see from malicious macOS installers by including JavaScript commands within the package file’s Distribution definition XML file. This produces a different telemetry pattern:
- Parent process: Installer
- Process: bash
As with preinstall and postinstall scripts, this telemetry pattern isn’t enough to identify malicious behavior on its own. Preinstall and postinstall scripts include command-line arguments that offer clues into what’s actually getting executed. The malicious JavaScript commands, on the other hand, run using the legitimate macOS Installer process and offer very little visibility into the contents of the installation package or how that package uses the JavaScript commands.
We know that the malware was installed via Apple installer packages (.pkg files) named update.pkg or updater.pkg. However, we do not know how these files were delivered to the user.
These .pkg files included JavaScript code, in such a way that the code would run at the very beginning, before the installation has really started. The user would then be asked if they want to allow a program to run “to determine if the software can be installed.”
Silver Sparrow’s installer telling the user:
“This package will run a program to determine if the software can be installed.”
This means that, if you were to click Continue, but then think better of it and quit the installer, it would be too late. You’d already be infected.
Another indication of malicious activity was the PlistBuddy process creating a LaunchAgent on your Mac.
LaunchAgents provide a way to instruct launchd, the macOS initialization system, to periodically or automatically execute tasks. They can be written by any user on the endpoint, but they will usually also execute as the user that writes them.
There are multiple ways to create property lists (plists) on macOS, and sometimes hackers use different methods to achieve their needs. One such way is through PlistBuddy, a built-in tool that allows you to create various property lists on an endpoint, including LaunchAgents. Sometimes hackers turn to PlistBuddy to establish persistence, and doing so enables defenders to readily inspect the contents of a LaunchAgent using EDR because all the properties of the file get shown on the command line before writing.
In Silver Sparrow’s case, these are the commands writing the content of the plist:
- PlistBuddy -c “Add :Label string init_verx” ~/Library/Launchagents/init_verx.plist
- PlistBuddy -c “Add :RunAtLoad bool true” ~/Library/Launchagents/init_verx.plist
- PlistBuddy -c “Add :StartInterval integer 3600” ~/Library/Launchagents/init_verx.plist
- PlistBuddy -c “Add :ProgramArguments array” ~/Library/Launchagents/init_verx.plist
- PlistBuddy -c “Add :ProgramArguments:0 string ‘/bin/sh'” ~/Library/Launchagents/init_verx.plist
- PlistBuddy -c “Add :ProgramArguments:1 string -c” ~/Library/Launchagents/init_verx.plist
The LaunchAgent Plist XML will resemble the following:
Label
init_verx
RunAtLoad
true
StartInterval
3600
ProgramArguments
‘/bin/sh’
-c
“~/Library/Application\\ Support/verx_updater/verx.sh” [timestamp] [data from plist downloaded]
Silver Sparrow also includes a file check that causes the removal of all persistence mechanisms and scripts by checking for the presence of ~/Library/._insu on disk. If the file is present, Silver Sparrow removes all of its components from the endpoint. Hashes reported from Malwarebytes (d41d8cd98f00b204e9800998ecf8427e) indicated that the ._insu file was empty.
if [ -f ~/Library/._insu ]
then
rm ~/Library/Launchagents/verx.plist
rm ~/Library/Launchagents/init_verx.plist
rm /tmp/version.json
rm /tmp/version.plist
rm /tmp/verx
rm -r ~/Library/Application\\ Support/verx_updater
rm /tmp/agent.sh
launchctl remove init_verx
At the end of the installation, Silver Sparrow executes two discovery commands to construct data for a curl HTTP POST request indicating that the installation occurred. One retrieves the system UUID for reporting, and the second finds the URL used to download the original package file.
By executing a sqlite3 query, the malware finds the original URL the PKG downloaded from, giving the cybercriminals an idea of successful distribution channels. We usually see this kind of activity with malicious adware on macOS: sqlite3 sqlite3 ~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV* ‘select LSQuarantineDataURLString from LSQuarantineEvent where LSQuarantineDataURLString like “[redacted]” order by LSQuarantineTimeStamp desc’
How to Remove Silver Sparrow Malware from Mac

Apple quickly took steps to override the developer certificates that enabled the Silver Sparrow malware to be installed. Further installations should therefore no longer be possible.
Apple’s customers are usually protected from malware because all software downloaded outside of the Mac App Store is required to be notarized. In this case it seems that the malware writers were able to obtain a certificate that was used in order to sign the package.
Without this certificate the malware can no longer infect more computers.
Another way of detecting Silver Sparrow is by searching for the presence of indicators to confirm whether you are dealing with a Silver Sparrow infection or something else:
- Look for a process that appears to be PlistBuddy executing in conjunction with a command line containing the following: LaunchAgents and RunAtLoad and true. This analytic helps find multiple macOS malware families establishing LaunchAgent persistence.
- Look for a process that appears to be sqlite3 executing in conjunction with a command line that contains: LSQuarantine. This analytic helps find multiple macOS malware families manipulating or searching metadata for downloaded files.
- Look for a process that appears to be curl executing in conjunction with a command line that contains: s3.amazonaws.com. This analytic helps find multiple macOS malware families using S3 buckets for distribution.
The presence of these files also indicate that your device has been compromised with either version 1 or version 2 of the Silver Sparrow malware:
- ~/Library/._insu (empty file used to signal the malware to delete itself)
- /tmp/agent.sh (shell script executed for installation callback)
- /tmp/version.json (file downloaded from from S3 to determine execution flow)
- /tmp/version.plist (version.json converted into a property list)
For Malware Version 1:
- File name: updater.pkg (installer package for v1) or updater (bystander Mach-O Intel binary in v1 package)
- MD5: 30c9bc7d40454e501c358f77449071aa or c668003c9c5b1689ba47a431512b03cc
- s3.amazonaws[.]com (S3 bucket holding version.json for v1)
- ~/Library/Application Support/agent_updater/agent.sh (v1 script that executes every hour)
- /tmp/agent (file containing final v1 payload if distributed)
- ~/Library/Launchagents/agent.plist (v1 persistence mechanism)
- ~/Library/Launchagents/init_agent.plist (v1 persistence mechanism)
- Developer ID Saotia Seay (5834W6MYX3) – v1 bystander binary signature revoked by Apple
For Malware Version 2:
- File name: update.pkg (installer package for v2) or tasker.app/Contents/MacOS/tasker (bystander Mach-O Intel & M1 binary in v2)
- MD5: fdd6fb2b1dfe07b0e57d4cbfef9c8149 or b370191228fef82635e39a137be470af
- s3.amazonaws[.]com (S3 bucket holding version.json for v2)
- ~/Library/Application Support/verx_updater/verx.sh (v2 script that executes every hour)
- /tmp/verx (file containing final v2 payload if distributed)
- ~/Library/Launchagents/verx.plist (v2 persistence mechanism)
- ~/Library/Launchagents/init_verx.plist (v2 persistence mechanism)
- Developer ID Julie Willey (MSZ3ZH74RK) – v2 bystander binary signature revoked by Apple
To delete the Silver Sparrow malware, these are the steps you can do:
1. Scan using an anti-malware software.
The best defense against malware on your computer will always be a reliable anti-malware software such as Outbyte AVarmor. The reason is simple, an anti-malware software scans your entire computer, locates and removes any suspicious programs no matter how well hidden they are. Removing malware manually might work, but there is always the chance that you might miss something. A good anti-malware program does not.
2. Delete Silver Sparrow programs, files and folders.
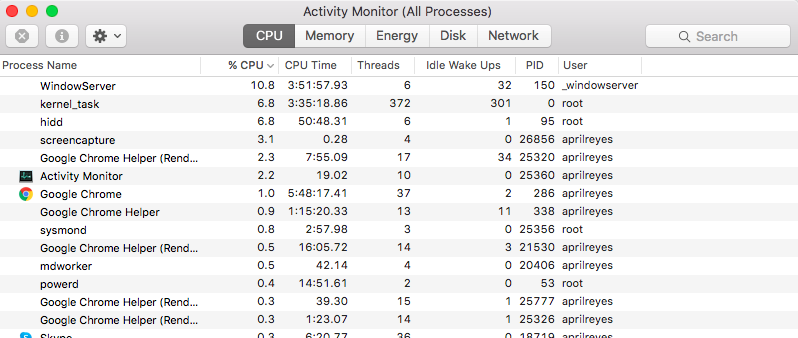
To delete the Silver Sparrow malware on your Mac, first navigate to the Activity Monitor and kill off any suspicious processes. Otherwise, you will be getting error messages when you try to delete it. To get to the Activity Monitor, take the following steps:
- Open Finder.
- Go to Applications > Utilities > Activity Monitor.
- On the Activity Monitor, look for the processes that are running. If any of them appears suspicious or unfamiliar, quit it. For further scrutiny of the process, you can highlight it with the mouse and right-click on it to see file location.
After you have deleted any suspicious programs, you will also have to delete the malware-related files and folders. The following are the steps to take:
- Using the Finder’s Go to Folder option, navigate to /Library/LaunchAgents folder. Inside this folder, look for any suspicious files that are associated with Silver Sparrow. Examples of files of this nature include “myppes.download.plist”, “mykotlerino.ltvbit.plist” and “installmac.AppRemoval.plist”. To help with the identification, look for files with common strings.

- Use Finder to navigate to the /Library/Application Support folder. Here, look for suspicious files, especially the ones related to applications that you deleted using the Applications app. Removing these will stop Silver Sparrow from resurfacing in the future.

- Navigate to the /Library/LaunchDaemons folder and look for any suspicious files. Examples of suspicious files that are associated with the Silver Sparrow malware include “com.myppes.net-preferences.plist”, “com.kuklorest.net-preferences.plist”, “com.aoudad.net-preferences.plist” and “com.avickUpd.plist”. Move these files to the trash.

3. Uninstall any Silver Sparrow browser extensions, if applicable.
After manually deleting the malware from your computer’s hard drives, you will also need to uninstall any Top Results browser extensions. Go the Settings > Extensions on the browser that you are using and remove any extensions that you are not familiar with. Alternatively, you can reset your browser to default as this will also remove any extensions.
Summary
The Silver Sparrow malware remains mysterious because it does not download additional payloads even after a long time. This means that we do not have an idea what the malware was designed to do, leaving Mac users and security experts puzzled about what it is meant to do. Despite the lack of malicious activities, the presence of the malware itself poses a threat to the infected devices. Hence, it should be removed immediately and all traces of it should be deleted.



Vicrey, I don’t see clear notation of what files I would look for on the mac monitor. Generic “suspicious files” is not enough guidance.
I really like your emphasis on “we really don’t know what it is going to do” one day.
Many thanks for your articles